This website uses cookies for security purposes only. We do not track you or see your data.
technical
-

Autodafe fuzzer compile fix
I wanted to take a look at an old fuzzer called AutoDafe because its name popped up in several papers…
-

DLink dir655 rev B firmware reverse engineering – part 1
Intro Recently I stumbled upon Paul dot com blog post Reverse Engineering Firmware Primer and decided to see if I…
-

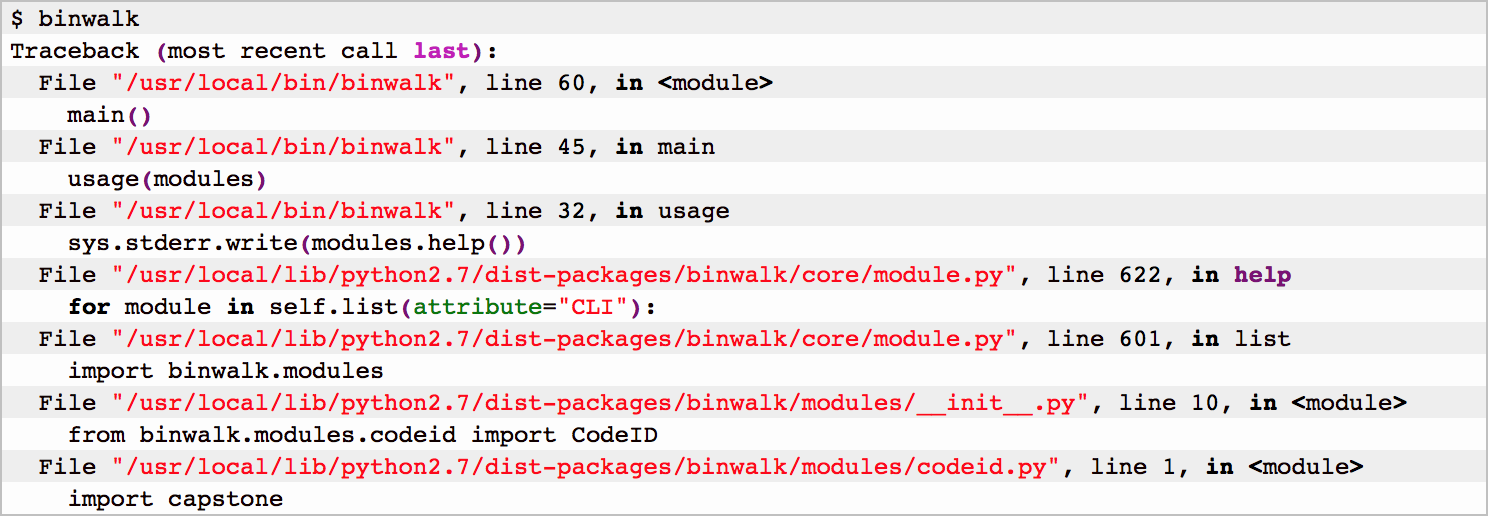
Setting up capstone (Debian Wheezy)
Intro Recently I’ve decided to dedicate a fresh Debian environment for my RE tools and having binwalk seemed as a…
-

Practical Reverse Engineering Exercises – Ch1-Ex2 – Write-Up
Intro This is the second post of a blog series following my progress with the “Practical Reverse Engineering: x86, x64,…
-

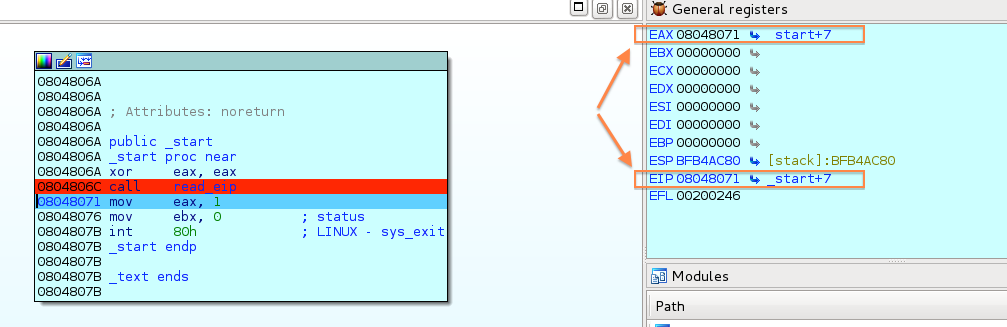
Practical Reverse Engineering Exercises – Ch1-Ex1 – Write-Up
Intro This is the first post of what should be a blog series following my progress with the “Practical Reverse…
-

D3 experiments: Simple vulnerability summary representation
19 May Update I have improved a bit the host representation. Digging into d3 capabilities found several very useful capabilities…
-

How to emulate Gaussian blur in iDraw
I am sorry but this is not a security related blog post. However I still consider some workarounds as “life…
-

Vulnerable web applications to play with
This is just a list with applicaitons and frameworks out there that could be used to test your web application…
-

Doxygen & PHP static code analysis call graphs
This post is more to document my own “discovery” and not to get into the loop of researching the same…
-

HTTP Basic Authentication Dictionary and Brute-force attacks with Burp Suite
HTTP Basic Authentication brief explanation HTTP supports several authentication mechanisms. Upon a request for resource within a protected space the…