This website uses cookies for security purposes only. We do not track you or see your data.
-

Practical Reverse Engineering Exercises – Ch1-Ex2 – Write-Up
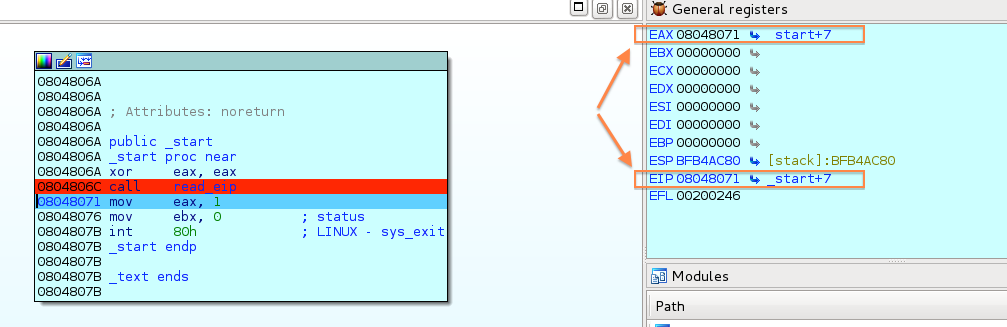
Intro This is the second post of a blog series following my progress with the “Practical Reverse Engineering: x86, x64,…
-

Practical Reverse Engineering Exercises – Ch1-Ex1 – Write-Up
Intro This is the first post of what should be a blog series following my progress with the “Practical Reverse…
-

D3 experiments: Simple vulnerability summary representation
19 May Update I have improved a bit the host representation. Digging into d3 capabilities found several very useful capabilities…
-
 Information Security Management and Governance, Learning and Information Security Career Development
Information Security Management and Governance, Learning and Information Security Career DevelopmentNice Software Vulnerability Management white paper by Chad Butler – Mind maps
Your external security consultant just sent you the vulnerability report from the last test you ordered? What shall you do…
-

How to emulate Gaussian blur in iDraw
I am sorry but this is not a security related blog post. However I still consider some workarounds as “life…
-

Cool visualisation ideas
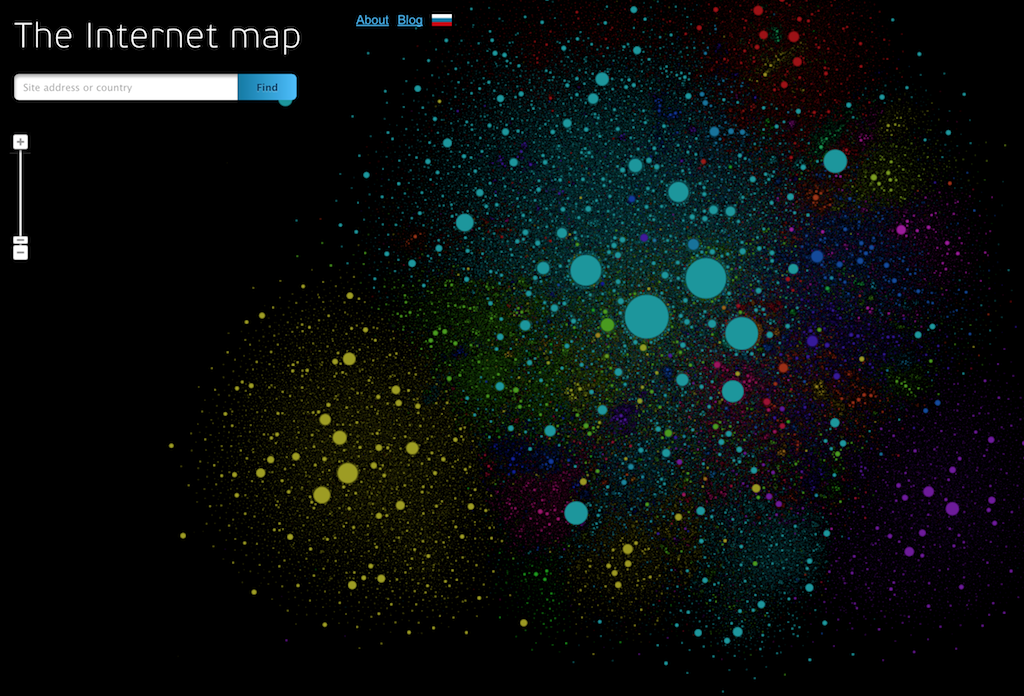
I have always admired people that could represent complex ideas in a simple way or have come up with ideas…
-

Vulnerable web applications to play with
This is just a list with applicaitons and frameworks out there that could be used to test your web application…
-

Doxygen & PHP static code analysis call graphs
This post is more to document my own “discovery” and not to get into the loop of researching the same…
-

Fix the problem, not just point at it – thoughts on the “bug hunting” initiatives etc.
I have been thinking a lot about the fact that the panetesting, sourco code reviews and all those security assurance…
-

Visualise your Apache logs with logstalgia
Couple of days ago a colleague of mine (thanks DL) got my attention with a lovely web server access log…