This website uses cookies for security purposes only. We do not track you or see your data.
Security Operations
-

DLink dir655 rev B firmware reverse engineering – part 1
Intro Recently I stumbled upon Paul dot com blog post Reverse Engineering Firmware Primer and decided to see if I…
-

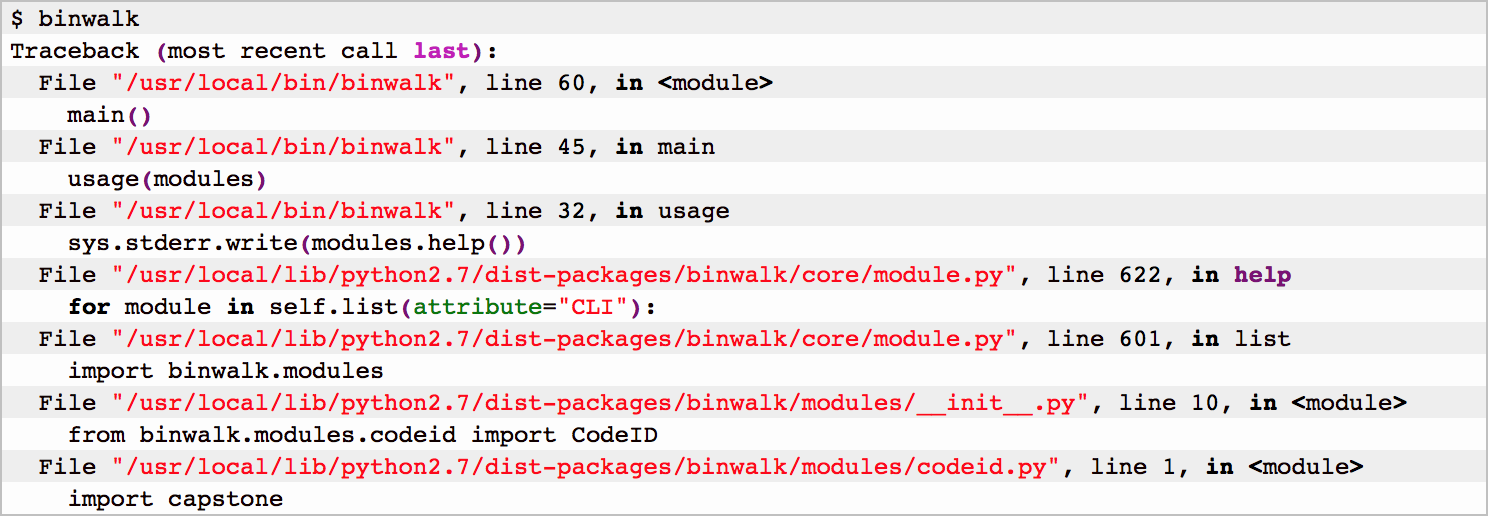
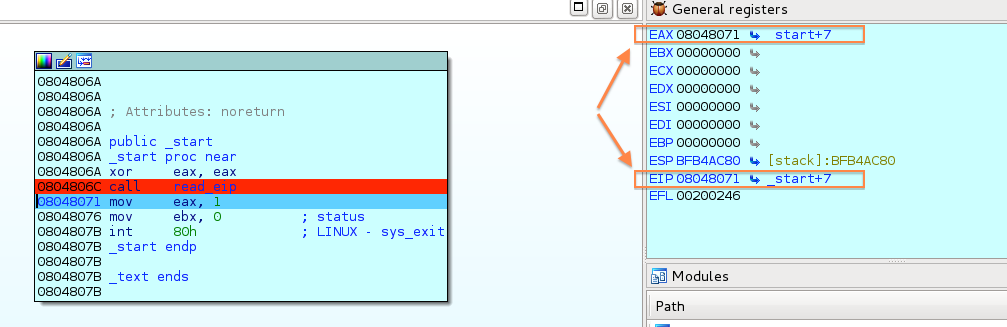
Setting up capstone (Debian Wheezy)
Intro Recently I’ve decided to dedicate a fresh Debian environment for my RE tools and having binwalk seemed as a…
-

Practical Reverse Engineering Exercises – Ch1-Ex2 – Write-Up
Intro This is the second post of a blog series following my progress with the “Practical Reverse Engineering: x86, x64,…
-

Practical Reverse Engineering Exercises – Ch1-Ex1 – Write-Up
Intro This is the first post of what should be a blog series following my progress with the “Practical Reverse…
-

Fix the problem, not just point at it – thoughts on the “bug hunting” initiatives etc.
I have been thinking a lot about the fact that the panetesting, sourco code reviews and all those security assurance…
-

Visualise your Apache logs with logstalgia
Couple of days ago a colleague of mine (thanks DL) got my attention with a lovely web server access log…
-

Saving data from “dying” HDD – LVM & ext3
Couple of days I restarted my machine running Debian Wheezy and for my surprise I was not able to boot….
-

Malware Sandbox – Free Public Cuckoo instance
I’m writing this down for my own reference and if someone else benefits this I’ll be more than happy. Here…
-

HTTP Basic Authentication Dictionary and Brute-force attacks with Burp Suite
HTTP Basic Authentication brief explanation HTTP supports several authentication mechanisms. Upon a request for resource within a protected space the…
-

forum.arenabg.com members table dumped and published in the Internet
Yesterday a partial dump containing email addresses and hashed passwords for the forum.arenabg.com members leaked. According to The Hackers News…