SecureDrop is a great tool and the to-go open-source solution for organisations opening an anonymous tip line for whistleblowers. It has been around for years (10 in fact) and is used by many media and public sector organisations.
The benefits SecureDrop provides in terms of secure communication and anonymity can be invaluable for investigative journalism. For this reason not only big media organisations but also small and midsize investigative journalistic teams consider using it. However, it’s essential for small teams to carefully consider the resources and expertise required to set up and maintain a SecureDrop instance.
This short blog post aims to shed light on common questions I have been asked by people considering using the platform. It does not aim to replace SecureDrop documentation but rather compliment the wonderful SecureDrop FAQ section that you should definitely read.
Briefest SecureDrop history ever
SecureDrop has its origins in a project called “DeadDrop,” created by the late Aaron Swartz and journalist Kevin Poulsen in 2012. Swartz’s goal was to develop a secure and anonymous platform for whistleblowers to submit information to journalists. After Swartz’s untimely death in 2013, the Freedom of the Press Foundation (FPF) adopted the project, renamed it “SecureDrop”, and began maintaining and improving the platform as well as maintaining extensive documentation.
Setting up SecureDrop instance
SecureDrop is a software and a self-hosted solution i.e. you will need to think about owning and maintaining hardware. This means
- procuring hardware — servers, firewall and workstations (check FPF FAQ for cost estimate) — if you are not confident in the system administration skills your team has, I would strongly advise sticking to recommended FPF hardware. That would save you pain in the long run.
- where you are to keep the hardware and its physical security — consider the location and the options to keep the servers away from accidental or intentional damage risks.
- how you are to connect your infrastructure to the Internet — separate to your corporate line is recommended
- protocols in force majeure situation where you might need to move the system physical location
- you should definitely seek legal advise to assess your legal risks depending on the jurisdictions your organisation is subject of.
You will need some system infrastructure skills in your team and a person (preferably people) comfortable with Linux (SecureDrop uses Ubuntu Server for servers and Tails OS for workstations), having some experience configuring network devices, some understanding of Tor network and asymmetric encryption (GPG specifically).
The initial system setup is straight forward and entails installing servers and workstations components, generating encryption keys etc. All this is could be achieved by following the very detailed FPF documentation. I would suggest the people dedicated to the project familiarise themselves with the documentation upfront. It is indeed very detailed but it is a must to understand how the different components work together.
SecureDrop uses OSSEC as log monitoring and host intrusion detection systems. During the configuration you will need to provide email address to which the deployment will be sending encrypted email notifications about security and health relevant events.
TIP: Consider using a dedicated email address for this communication so you do not miss stuff.
Publishing your SecureDrop instance address
To provide level of anonymity SecureDrop interfaces are available over ToR only. During the installation of your servers, ToR addresses will be assigned to the different SecureDrop interfaces.
The source interface is the end-user interface that potential sources will access and you will need its address advertised in a trustworthy manner i.e. hosting controlled by you. FPF suggests organisations create and host so called Landing page as one of their official website pages assuming you are the only one in control of its content. FPF also provides guidance on what the page should include and what security criteria it should meet. FPF also maintains a list active SecureDrop deployments which you could apply to be included in.
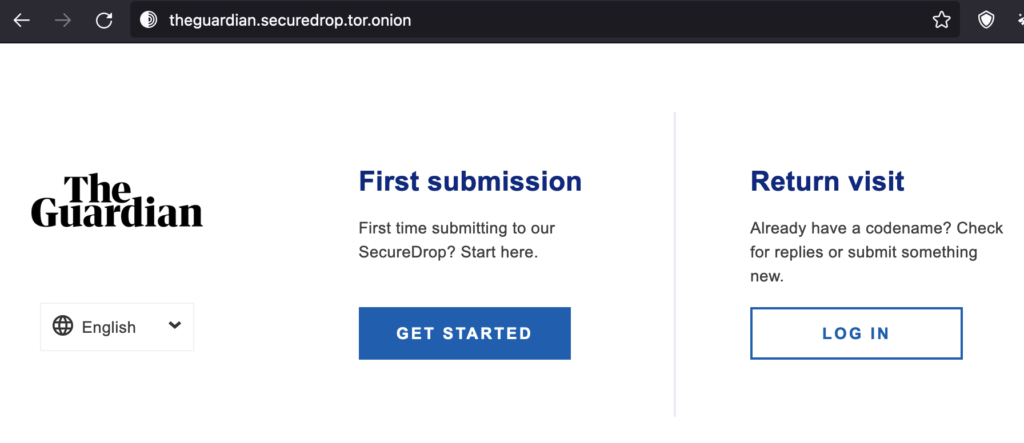
As you know ToR addresses are long and random strings which are not really memorable. If you want to have a more user-friendly address — FPF offers to organisation use of memorable onion aliases where FPF maintains a mapping between the friendly onion name and the long ToR address of your instance. Its worth nothing that this alias has dependency on Tor project maintaining certain browser features and it currently works only for desktop Tor browser but not for mobile versions. You would also have a dependency on FPF. The screen bellow shows The Guardian SecureDrop instances loaded using onion name.
TIP: Do consider how these dependencies agree with your risk appetite.
Maintaining SecureDrop infrastructure
Maintaining the infrastructure is relatively straight forward, not too time consuming and is usually not much of a hustle. The main elements you need to take care of are:
- updates SecureDrop servers— this will require minimal effort on your side because FPF has automated the process so in most cases your servers will just pick the latest update (when available). It is important to always read the version release notes issued by FPF so you are prepared for eventualities.
- update SecureDrop workstations (there are number of these)— this requires more discipline on your side and will consists of 1) updated of the operating system — keep an eye on Tails updates 2) SecureDrop workstation version updates — you will usually get prompted when you fire-up your workstation and connect to ToR and if a new SecureDrop workstation version is available. Updates could be easy or not so easy to apply depending on how behind you are with versions.
TIP: create a habit to dedicate weekly slot to check for updates and apply them if needed. Tiny bit of discipline will save you some grief in the long run. - update the firewall— regardless which firewall you use it would require regular updates (software and firmware) to ensure you keep it as secure as possible. This operation will be usually more time consuming and in general with higher chance of something going wrong.
TIP (s): 1) Since the firewall sits in front of your instances, issues with the upgrade might render the SecureDrop platform unavailable to your users. Make sure that you alocate maintainance slot and you notify your user base — more on platform availability monitoring later. 2) Make sure you have a record of your configuration in some form which is readily available for manual recovery. Always try to back up/restore configuration before update. If you use pfSense that is especially important — I had some painful experiences with upgrade process and also with backup/restore from backup — in this cases configuration record - backing up the server config and data — to minimise interruption in operation you will need to backup your servers on regular basis. You could backup both configuration and data. Depending on the age of your system, and the sizes of the stored submission the backups could bulk up in size.
TIP: if your backups are too big it would be painful to pull them over ToR (which is the default backup process). If that is the case you might need to consider transferring backups by directly connecting backup drive to your server instance. Before doing so consider the security implications and seek advise if needed from FPF. - monitor the OSSEC alerts — you will receive email alerts only for OSSEC levels 7 and above. Most of the ales will be mundane but build a discipline to review them.
TIP: if you see alert level 12 you must pay close attention.
Important operational considerations
There are quite few operational elements that you will need to consider sooner or later. I will highlight the most important ones.
Key management
SecureDrop heavily relies on GPG to encrypt information submitted by sources as well as for encrypting security relevant events sent to your administrators. Certain keys will need to be issued and available for specific purposes to decrypt information sent to your administrators or journalists. The relevant private keys and the associated credentials will need to be stored and managed securely so you will need to decide how access to thee keys would be managed. In addition on-boarding and off-boarding staff members will require key rotation. This comes as additional head-over.
Submissions review and dealing with noise/spam/malware
All submission sent through the SecureDrop source interface are encrypted with a single public key pair. The submissions are reviewed from a dedicated secure viewing workstation(s) which keep the private counterpart of the submission key and are supposed to be air gapped. This means that you will need to carefully review the SecureDrop dataflow and consider how you are to organise your process around reviewing submissions and transferring information out of the viewing station.
One important element to note is that SecureDrop is not immune to spam and other submissions that could be categorised as noise. The more popular your instance is the higher are the chances you will receive more noise. You will need to factor time and human resource to review submissions.
In addition you need to consider the potential malicious nature of files submitted to you via the source interface. Setting up reliable sanitisation process to ensure malware does not creep up into your systems is vital.
Training
All SecureDrop users will need to be trained to use the system and this must not be overlooked. If you do not have internal know-how reach out to FPF who could help with training.
Expect the unexpected
As any technical solution SecureDrop could throw you an unexpected challenge and sometimes it might not be straight forward to resolve your problem.
TIP: I would strongly advise any organisation that considers running SecureDrop as part of its newsroom tooling to secure a paid support with FPF. The foundation annual charge is extremely reasonable and the team help could be invaluable.
Closing words
Although SecureDrop initial setup is not overly costly or complicated its secure operations over time requires dedication and commitment as well as level of discipline. If you are considering running your own instance as part of your investigative journalism tooling I would encourage you to reach out to organisations that have been running SecureDrop for few years as well as to FPF. Have an honest conversation around the cost of the operations as time, effort and skill so you can inform your own decision making.




Leave a Reply