This website uses cookies for security purposes only. We do not track you or see your data.
Year: 2014
-

Autodafe fuzzer compile fix
I wanted to take a look at an old fuzzer called AutoDafe because its name popped up in several papers…
-

Maritime Cybersecurity Mind Map
Recently I have been researching the cyber threats in the maritime industry, what has been done and which areas are…
-

Stack canaries cartoon
Lately I have been busy studying different buffer overflow protection mechanisms and while reading about stack canaries a funny picture…
-

DLink dir655 rev B firmware reverse engineering – part 1
Intro Recently I stumbled upon Paul dot com blog post Reverse Engineering Firmware Primer and decided to see if I…
-

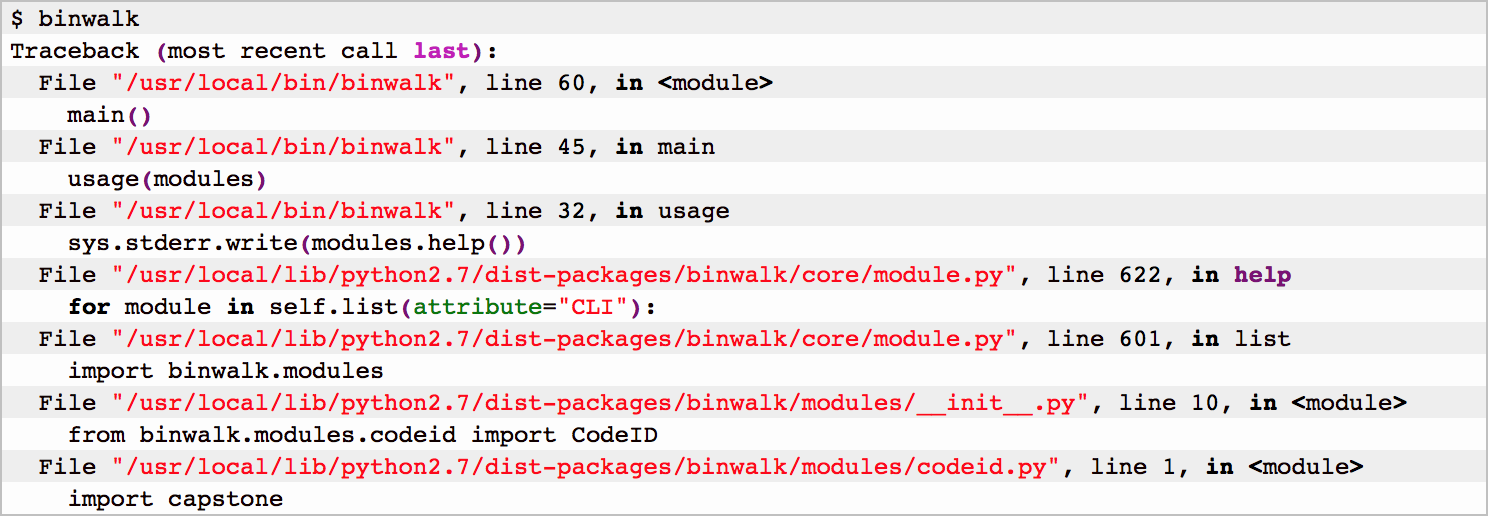
Setting up capstone (Debian Wheezy)
Intro Recently I’ve decided to dedicate a fresh Debian environment for my RE tools and having binwalk seemed as a…
-

Practical Reverse Engineering Exercises – Ch1-Ex2 – Write-Up
Intro This is the second post of a blog series following my progress with the “Practical Reverse Engineering: x86, x64,…
-

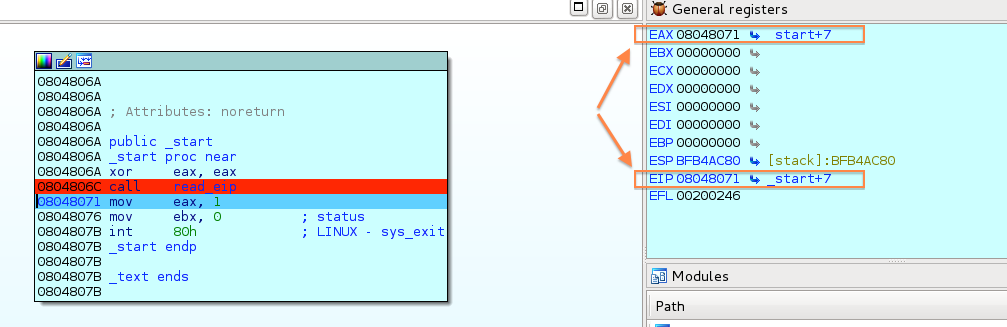
Practical Reverse Engineering Exercises – Ch1-Ex1 – Write-Up
Intro This is the first post of what should be a blog series following my progress with the “Practical Reverse…
-

D3 experiments: Simple vulnerability summary representation
19 May Update I have improved a bit the host representation. Digging into d3 capabilities found several very useful capabilities…
-

Nice Software Vulnerability Management white paper by Chad Butler – Mind maps
Information Security Management and Governance, Learning and Information Security Career DevelopmentYour external security consultant just sent you the vulnerability report from the last test you ordered? What shall you do…