This website uses cookies for security purposes only. We do not track you or see your data.
Year: 2012
-

GDBOP website malfunctioning … again
I just found out, with no surprise, that the website of GDBOP (Bulgarian government cybersecurity team) hosted on http://www.cybercrime.bg does…
-

Security source code review scoping questionnaire
Usually when a customer comes with request for security source code review one of the main questions is “How long…
-

Teach your students to cheat
In one of his latest posts Bruce Schneier refers to an interesting article authored by two Marylend University professors. They…
-

An Introduction To Keyloggers, RATS And Malware – book review
Yesterday I stumbled across yet another “hacking” site. My curiosity motivated me to mirror the site content and go through…
-

Udacity – nice online computer science courses
A post outside the security field … A friend of mine sent me a link to the http://www.udacity.com/ (Thanks, Momcho!) and after…
-

Kaspersky Lab source code analysis of Duqu
Kaspersky Lab has been analysing the infamous duqu worm code for several months. In one of the latest writeups, Igor…
-

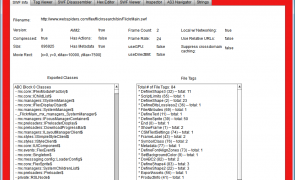
SWFInvestigator – a new tool for testing SWF files
Three days ago Adobe Labs surprised me with a beta version of their opensource Air application for SWF analysis called…
-

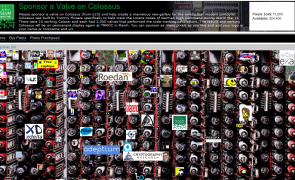
Colossus gallery fundraising initiative
British national museum of computing started conversation work of the Colossus hall. Colossus is one of the first programmable computers…
-

Zero day exploits officially on sail
The 0-day exploits market was there for some time, but it was always a underground black hats territory. I’m sure…
-

Hacking Lab – how and why
In one of the recent Ethical Hacking Network articles, Thomas Whilhelm, the founder of hackingdojo.com, discusses questions regarding setting up…